| Web Application Security | ||
|---|---|---|
| Previous | Next | |
| Instant module | Apache Solr Search Server | |
For the iKnowBase web server, the default configuration will be
If you are installing on Oracle WebLogic, the default will be
If you need to customize authentication, the basic steps are
The iKnowBase web application security implementation is based on the Spring Security framework and takes care of user authentication and authorization to specific web application protected areas.
An authentication module combines authentication methods with authentication providers.

Whereas an authentication mechanism defines how the client interacts with the system to provide the necessary credentials for authentication, the authentication provider verifies the credentials and, if verified, creates the authentication object for the application. The authentication object are then evaluated by the authorization rules associated with the requested resource.
The authentication process follows this flow:
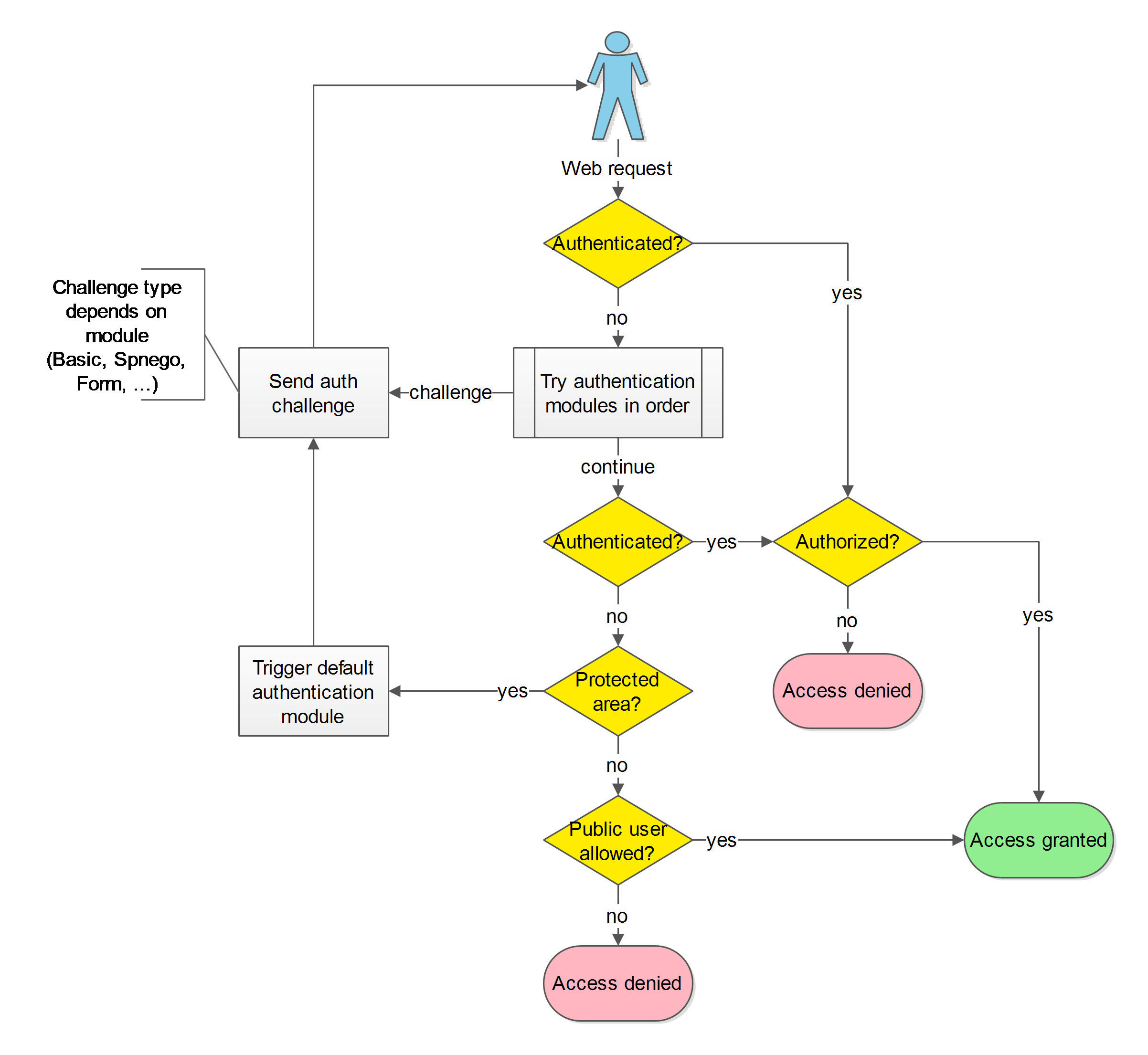
The authentication modules may authenticate the user based on the incoming web request or start a authentication challenge flow.
ALL authentications will ultimately be verified by loading and verifying the user from the iKnowBase User Repository.
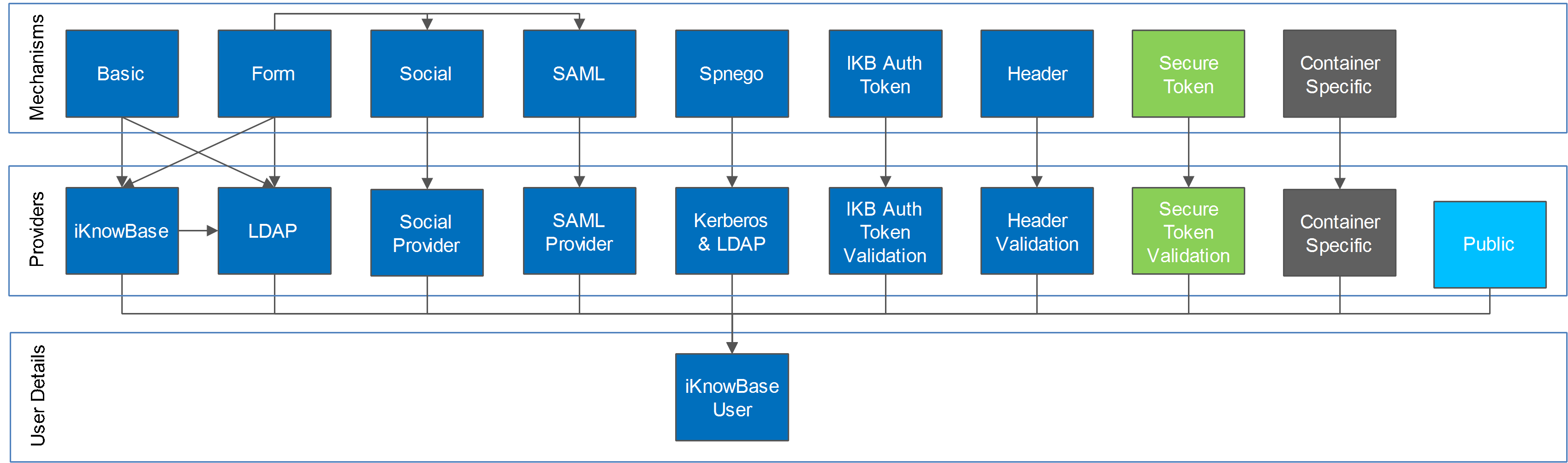
Multiple authentication modules (mechanisms and providers) are supported and can be activated at the same time. One is set as the default and the other active modules may be explicitly triggered. This image provides an overview of the possible combinations:
Web Application Security is configured using configuration properties .
See iKnowBase Installation Guide > Configuration > Spring Security Configuration for detailed configuration options.
When the users enters a protected area, the default authentication module will be triggered and as part of the authentication process challenge the user for user credentials.
When no explicit default module has been set, the following defaults apply:
| Application Server | Modules | Authentication module | Authentication method | Authentication provider | Comment |
|---|---|---|---|---|---|
| iKnowBase web server | * | Form | Form | iKnowBase User repository | |
| iKnowBase web server | Instant | Basic | Basic | iKnowBase User repository | Due to client compatibility. |
| Oracle WebLogic | * | Container | Container dependant | Container dependant |
“simple authentication” in this section refers to the following authentication mechanisms in prioritized order (first enabled wins)
iKnowBase Instant requires “simple authentication” if you want to use the
/private Instant endpoint and this is therefore set as the default. If not, you may reconfigure and use other modules such as Form based authentication.
Form based authentication for WebDAV uses the MS-OFBA protocol. See WebDAV specific configuration options for form based authentication.
A client may trigger a specific type of authentication other than the configured default. iKnowBase supports triggering a specific mechanism using the either path
/ikb$auth/<authentication mechanism>/authenticate or HTTP request header
X-IKB-AUTH.
As an example, while the default authentication is form based, a client may trigger the HTTP Basic mechanism by accessing
/ikb$auth/basic/authenticate or by issuing the HTTP request header
X-IKB-AUTH: Basic.
Note: Path trigger has lower case “basic”, but header and default module setting has the initial letter in uppercase “Basic”.
Available authentication mechanisms:
| Authentication mechanism | Path trigger | Header trigger | Can be used as default | Authentication provider | Description |
|---|---|---|---|---|---|
| Basic | /ikb$auth/basic/authenticate | X-IKB-AUTH: Basic | YES | UsernamePassword | Basic authentication for username and password. |
| Container | /ikb$auth/container/authenticate | X-IKB-AUTH: Container | YES (WebLogic only) | Container | Container based authentication (depends on security setup in the application server). |
| Form | /ikb$auth/form/authenticate | X-IKB-AUTH: Form | YES | UsernamePassword, Social, Saml | Form based authentication. |
| FormWebdav | /ikb$auth/formWebdav/authenticate | X-IKB-AUTH: FormWebdav | YES (WebDAV only) | UsernamePassword, Social, Saml | Form based authentication for WebDAV (MS-OFBA protocol authentication page traffic). |
| Msofba | /ikb$auth/msofba/authenticate | X-IKB-AUTH: Msofba | YES (WebDAV only) | UsernamePassword, Social, Saml | Form based authentication for WebDAV (MS-OFBA protocol WebDAV traffic). |
| AutoForm | /ikb$auth/autoform/authenticate | N/A | YES | UsernamePassword | Form based authentication using an autogenerated login form (handy as a backup if the normal login form is out of order). |
| Header | /ikb$auth/header/authenticate | X-IKB-AUTH: Header | YES | Header validation | Request header based authentication. |
| Spnego | /ikb$auth/spnego/authenticate | X-IKB-AUTH: Spnego | YES | Kerberos realm and LDAP | SPNEGO based authentication for Kerberos single sign on (i.e. Microsoft Windows domain single sign on). |
| Saml | /ikb$auth/saml/authenticate | X-IKB-AUTH: Saml | YES | SAML2 identity provider | SAML2 based authentication with SAML2 compatible identity providers (i.e. ADFS, Feide, Salesforce). |
| /ikb$auth/google | N/A | NO | Social connection | Uses form based module. Will verify a preexisting social connection (created using account activation link). | |
| /ikb$auth/twitter | N/A | NO | Social connection | Uses form based module. Will verify a preexisting social connection (created using account activation link). | |
| /ikb$auth/facebook | N/A | NO | Social connection | Uses form based module. Will verify a preexisting social connection (created using account activation link). | |
| /ikb$auth/linkedin | N/A | NO | Social connection | Uses form based module. Will verify a preexisting social connection (created using account activation link). | |
| Microsoft Live | /ikb$auth/live | N/A | NO | Social connection | Uses form based module. Will verify a preexisting social connection (created using account activation link). |
| iKB Secure Token | N/A | N/A | NO | Secure token validation | iKnowBase secure token based authentication. |
| iKB Auth Token | N/A | N/A | NO | Auth token validation | iKnowBase Auth token based authentication. |
| RememberMe | N/A | N/A | NO | RememberMe | Uses form based module. Will verify RememberMe cookies (created during form based login if checked). |
The authentication provider token “UsernamePassword” must be processed by an authentication provider capable of validating username and password.
All modules must ultimately validate the user against the iKnowBase User Repository using username lookup for an authentication to be considered successful.
iKnowBase supports multiple UsernamePassword providers for verifying the submitted username and password
Available authentication providers for UsernamePassword:
| Provider | Default enabled | Order | Description |
|---|---|---|---|
| LDAP | NO | 1 | LDAP user repository. |
| iKnowBase | YES | 2 | iKnowBase User repository. |
Both modules may be enabled at once and will be tried in the specified order.
An external account hosted by a SAML2 identity provider can be linked to an existing iKnowBase user account and used for authentication.
In the SAML module, iKnowBase acts as a service provider that authenticates the user with an identity provider.
Basic steps to enable iKnowBase as a service provider:
Basic steps to enable authentication with an identity provider:
SAML support is implemented using “spring-security-saml” ( Spring Security SAML documentation ).
A SAML account can be mapped to an iKnowBase account using either iKnowBase Auth Token or the auto connect feature.
iKnowBase auth token “ACTIVATION” is a one time token that can be issued to a pre-existing iKnowBase user. When such as token is used, the user can choose authentication method. After successful authentication with an external identity provider, the token is used to map the accounts.
The SAML auto connect feature can be used if the identity provider knows the iKnowBase user name and can issue this username attribute in the SAML response. iKnowBase will connect the accounts if a user was found with the specified username.
Note: Account connections leverage the social connection infrastructure. Existing connections per user can be viewed in administration console.
iKnowBase supports multiple identity providers. The user may choose identity provider using either the login form or SAML identity provider discovery mode.
The login form provided with iKnowBase will add login buttons for each configured identity provider. The login form may be fully custom implemented.
The discovery mode redirects the user to a discovery area where the default provided implementation displays a list of valid identity providers. The user may choose a provider and start the authentication process. The discovery area also takes an optional parameter that specifies which identity provider to use and will, if specified, start the authentication process automatically. The discovery area can be fully customized and allow custom automatic detection of the correct identity provider.
Multiple service providers may be specified and the default strategy for selecting a service provider is configured using the “spSelectionStrategy” option. The default strategy is to resolve using the request’s serverName, which normally will be the value of the HTTP Host header. An alternative is to use the alias path strategy where the Service Provider Entity ID must be present on the login path on the form .../alias/@localEntityId@.
SAML administration services:
| Path | Description |
|---|---|
| /ikb$auth/saml/display | Metadata web display (for iKnowBase service provider metadata). |
| /ikb$auth/saml/generate | Metadata generator (for iKnowBase service provider metadata). |
| /ikb$auth/saml/metadata | Metadata download URL (for iKnowBase service provider metadata). Supports additional alias=entityId path parameter if multiple SPs are present. |
SAML endpoints:
| Path | Description |
|---|---|
| /ikb$auth/saml/authenticate | Explicit SAML authentication trigger. Common iKnowBase auth trigger. |
| /ikb$auth/saml/discovery | IdP discovery service. |
| /ikb$auth/saml/login | Explicit SAML authentication trigger. Supports multiple SPs using “alias” path parameter. |
| /ikb$auth/saml/logout | Global logout. Use common /ikb$auth/logout for local logout. |
| /ikb$auth/saml/SingleLogout | Single Logout processing. (Called during global logout) |
| /ikb$auth/saml/SSO | Web Single Sign-on processing. (Called during single sign-on) |
| /ikb$auth/saml/HoKSSO | Web Single Sign-on Holder of Key processing. (Called during single sign-on) |
iKnowBase has been verified against these providers:
An external social account can be linked to an existing iKnowBase user account and used for authentication. iKnowBase supports multiple social providers.
The social authentication module requires that “Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files” are installed. Download and install “Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files” from http://www.oracle.com/technetwork/java/javase/downloads/index.html.
When enabling social authentication, you are required to set password and salt used for encrypting the secret user tokens received from the social provider.
Each social provider is configured and enabled separately and require that you configure them with the registered application id and secret. Refer to the social provider’s documentation for application registration.
Some social providers require that you specify the OAuth 2.0 Redirect
URL. Use
<absolute url to site><iknowbase-webapp contextPath>/ikb$auth/<providerid>. Example:
https://www.example.com/ikb$auth/google or
https://www.example.com/ikb$auth/google.
The iKnowBase Header authentication module supports authentication based on a trusted HTTP request header. This means that if you have a reverse proxy in front of iKnowBase that handles the authentication and is able provide the user name in a guaranteed and trusted HTTP request header, the user will be logged in to iKnowBase as well.
It is extremely important that the reverse proxy guarantees the header, meaning that if an end client (user) sends the trusted header it is to be discarded from the HTTP request and not be allowed to reach the iKnowBase web applications.
You may configure the header module with restrictions that must be satisfied before a header is trusted, like server name, ip-address and secret header sent by the reverse proxy.
iKnowBase supports a token called “ikbAuthToken” that can be used if the end user does not know the password associated with the account. The following types and privileges are supported:
| TokenType | Consumed after use | Privilege description |
|---|---|---|
| LOGIN | NO | Valid non expired token allows automatic login. |
| ACTIVATION | YES (successful only) | Valid non expired token allows the end user to choose between multiple authentication activation options. |
Tokens are generated using PL/SQL IKB_AUTH_API and used as URL parameter “ikbAuthToken”.
Example: http://www.example.com?ikbAuthToken=<the generated token>
Enables authentication with only a web link (no username, no password) as long as the has not expired.
WARNING: Anyone with a valid non expired trusted login token will be automatically logged in as the user associated with the token!
The available activation options are:
WARNING: Anyone with a valid non expired trusted activation token will be allowed to set password / connect using ANY external (social or saml) account!
Requests containing an activation token will be intercepted and will redirect the user to the link without the activation token after successfull activation.
Before an authenticated user has been established all enabled modules will examine the request for authentication information in the order they are defined. Some modules will only do so on specific paths (path scoped), while other modules will look no matter where the request is sent. A disabled module will skip processing.
If all modules are enabled, they will be called in the following order
| Module | Authentication token | Path scoped |
|---|---|---|
| ikbAuthToken | ikbAuthToken URL param | NO |
| Social Login | HTTP request for social login | /ikb$auth/ |
| Secure Token | _ikbUserToken HTTP header or URL param | NO |
| Header | HTTP header: [Configurable] | NO |
| Spnego | HTTP header: Authorization: Negotiate | NO |
| Container | Container dependant | Container dependant |
| Form | HTTP POST j_username, j_password | /j_spring_security_check |
| Basic | HTTP header: Authorization: Basic | NO |
| Saml | SAML2 messages | /ikb$auth/saml/* |
| RememberMe | HTTP RememberMe Cookie | NO |
| Public | NO |
Public authentication specific for iKnowBase will be used if no other authentication has been established and public access is allowed.
A client may have one of three privilege levels:
If a client uses the Public level and tries to access a web area that requires Normal authentication or higher, the user will be asked to authenticate.
The iKnowBase web applications have the following access requirements:
| Application | Area | Required level |
|---|---|---|
| iKnowBase Viewer | Default (NO ACL) | 1 |
| iKnowBase Viewer | ACL with public user | 1 |
| iKnowBase Authentication area | /ikb$auth | 2 |
| iKnowBase Viewer | ACL without public user | 2 |
| iKnowBase Viewer | /private | 2 |
| iKnowBase WebDAV | Default | 2 |
| iKnowBase WebServices | Default | 2 and TRUSTED |
| iKnowBase Administration console | /ikb$console | 3 |
iKnowBase WebServices requires that the user is registered as a trusted principal through membership in the trusted principal ACL. See iKnowBase Installation Guide > Configuration > Web Services Security Configuration for configuration details.
In addition content (web modules or documents) may also be protected by iKnowBase ACLs as discussed in iKnowBase Development Guide > Security Administration and iKnowBase User Administration Reference Guide > Access-Control-Lists .
A user receives administrator privileges if the user is flagged as an administrator in the iKnowBase User Repository, see iKnowBase User Administration Reference Guide > Users .
Restricting access in development toolkit is discussed in iKnowBase Development Guide > Development Toolkit > Security .
iKnowBase 6.5 and earlier versions required various roles for allowing access to the application, such as IKB_USERS, IKB_DEVELOPERS and IKB_SYSADMINS. These roles are no longer in use.
From iKnowBase 6.6 the security privileges are:
| Privilege | _Previous applicable role | Current requirement |
|---|---|---|
| Normal (2) | IKB_USERS | Any user that has authenticated and been verified as enabled in iKnowBase User Repository |
| Administrator (3) | IKB_DEVELOPERS, IKB_SYSADMINS | User marked as Admin in iKnowBase User Repository |
An authorized user may switch to a different identity. This can be used to greatly speed up troubleshooting as a administrator/developer can be granted permission to act as the user that reported the issue.
WARNING: Enabling switch user functionality can have severe security implications. Make sure these are understood and approved before activating this module.
Switch user support is enabled with (See configuration reference)
The access check procedure is mandatory and must have the following signature:
procedure [procedure_name] (
p_switch_user ot_switch_user,
p_return_code out number, // 0=PERMIT, others are user defined error codes
p_return_message out varchar2 // User defined error message
);
The input object ot_switch user is described below. A return code of 0 will allow access. Any other will deny access and both return code and return message will be logged.
Whenever a user switch to or exit from a user happens an INFO message will be logged and the optionally defined audit procedure will be called.
procedure [procedure_name] (
p_switch_user ot_switch_user
);
The
ot_switch_user object has the following properties:
| Property name | Value |
|---|---|
| authenticated_username | Username of the real authenticated user |
| switch_to_username | Username of the user that is being switched to |
| switch_type | 1=SWITCH, 2=EXIT (Only applicable for audit function |
When switch user has been enabled and configured, a user can switch by accessing the path
/j_spring_security_switch_user?j_username=[USERNAME TO SWITCH TO] and exit with path
/j_spring_security_exit_user. Both services supports an optional
redirect URL parameter that defaults to “/”.
A user may switch to different users provided access is granted for the switch. The maximum switch depth is 1, i.e. if USER1 has switched to USER2, the user may switch to USER3 provided USER1 is granted the switch. An implicit exit from USER2 is executed before the switch to USER3.
Logout service is available at
/ikb$auth/logout with an optional
redirect URL param, which supports both relative and absolute URLs.
Note that you are specifically authenticated for each deployed application. If you deploy iknowbase-webapp multiple times, then each will have a
/ikb$auth/logout service.
If you use Basic authentication, you may still logout, but the browser will automatically log in again if needed until the browser is closed.
If you use Spnego authentication, you may still logout, but the browser will automatically log in again if needed.
You may provide your own security implementation. Contact the iKnowBase Product Development team for implementation requirements.
This section covers common setup scenarios and explains the necessary setup. Refer to the Configuration section for detailed configuration names and options.
WebLogic: Note that container mode for WebLogic is supported and you may also as an alternative accomplish the required authentication using WebLogic’s own security modules. These examples does not cover detailed WebLogic container configuration.
This is most often done from inside ikbStudio, but for the first user you will have to do it using the command line:
cd /opt/iknowbase/production
./iknowbase.sh production.properties setIkbPassword orcladmin SECRETPASSWORD
You can now log in using the orcladmin user, with the password SECRETPASSWORD.
For the iKnowBase web server, this is the default. There is no need to change anything.
WebLogic only:
To use a custom login form instead of the default provided with iKnowBase, adjust the form module configuration with
Login form requirements for username and password:
Login form Social requirements:
Login form RememberMe requirements:
An authenticated sessions is valid for one web application only. If you deploy multiple applications, e.g. iknowbase-webapp-1, iknowbase-webapp-2, etc, the login form needs to POST to /j_spring_security_check relative to the Web Application you want to log in to.
RememberMe functionality can be used to cross application borders.
The Form login module will remember the original path that triggered authentication and redirect after successful login.
If you submit directly to j_spring_security_check without being redirected to a login form first, i.e. you have implemented login functionality on a public page, you will be redirected to /. You may use an additional parameter “redirect” to explicitly set the redirect location after successful login.
If you don’t want fallback to iKnowBase User Repository
The username mapped to iKnowBase user may also be set to any attribute name.
Given the user
DN: CN=My Name,CN=Users,DC=ad,DC=example,DC=com
sAMAccountName: MYNAME1234
someCustomAttribute: ORCLADMIN
You will be logged in to iKnowBase as “ORCLADMIN” when authenticating as “MYNAME1234”.
It is possible to configure iKnowBase to provide single sign-on authentication on Windows workstations that are already logged into Active Directory using the SPNEGO protocol. There are several steps to this process:
These main steps will be discussed in the following section
If you don’t want fallback to iKnowBase User Repository
Certain things needs to be known for SPNEGO to work. Let us assume the following configuration:
First, we need to make sure that the DNS (domain name system) is set up properly:
The reason for this requirement is that the web browser will use the canonical name when creating its secret “ticket”, which the server will then decode. It is therefore important that the client uses the name expected by the server. The configuration can be verified using the “ping” command on a client:
C:\>ping www.example.com
Pinging webserver-01.example.com [10.10.10.10] with 32 bytes of data:
Reply from 10.0.0.24: bytes=32 time=10ms TTL=63
...
C:\>ping intranett.example.com
Pinging webserver-01.example.com [10.10.10.10] with 32 bytes of data:
Reply from 10.0.0.24: bytes=32 time=10ms TTL=63
...
Internet Explorer will, by default, only attempt SPNEGO logins if the client uses a hostname without any dots. Thus, for maximum interoperatibiliy, make sure that it can reach the hosts “www” and “intranett”:
C:\>ping www
Pinging webserver-01.example.com [10.10.10.10] with 32 bytes of data:
Reply from 10.0.0.24: bytes=32 time=10ms TTL=63
...
C:\>ping intranett
Pinging webserver-01.example.com [10.10.10.10] with 32 bytes of data:
Reply from 10.0.0.24: bytes=32 time=10ms TTL=63
...
To enable SPNEGO for hostnames with dots, they must be added to IE’s Local Intranet Sites.
For the web server to be able to verify login requests, it will need to communicate with the active directory server. For that, it will need a dedicated user in active directory. The name of that user is arbitrary, but we recommend a name that matches the name of the webserver:
In active directory, create a user with the following properties:
On the active directory server, generate a keytab file for the user. The keytab file contains a username and password in encrypted format, and is used so that the web server can log in without specifying a password in a property file. The parameter to “-princ” is very important, and must follow this presice syntax: First the string “HTTP/”, then the canonical name of the web server, as seen by clients, and finally an at-sign followed by the active directory domain name.
C:\>ktpass -out iknowbase.webserver-01.example.com.krb5.keytab -princ HTTP/webserver-01.example.com@AD.EXAMPLE.COM -pass SecretPassword!GlobalMilk -mapUser iknowbase.webserver-01@AD.EXAMPLE.COM -pType KRB5_NT_PRINCIPAL -crypto ALL /kvno 0
Targeting domain controller: ad-server.example.com
Using legacy password setting method
Successfully mapped HTTP/webserver-01.example.com to webserver-01.example.com.
Key created.
Key created.
Key created.
Key created.
Key created.
Output keytab to webserver-01.example.com.krb5.keytab:
Keytab version: 0x502
keysize 68 HTTP/webserver-01.example.com@AD.IKNOWBASE.COM ptype 1 (KRB5_NT_PRINCIPAL) vno 0 etype 0x1 (DES-CBC-CRC) keylength 8 (0x80b685bf1f52ec5b)
keysize 68 HTTP/webserver-01.example.com@AD.IKNOWBASE.COM ptype 1 (KRB5_NT_PRINCIPAL) vno 0 etype 0x3 (DES-CBC-MD5) keylength 8 (0x80b685bf1f52ec5b)
keysize 76 HTTP/webserver-01.example.com@AD.IKNOWBASE.COM ptype 1 (KRB5_NT_PRINCIPAL) vno 0 etype 0x17 (RC4-HMAC) keylength 16 (0x8d32128c7d08747ccc61c3b343c93c47)
keysize 92 HTTP/webserver-01.example.com@AD.IKNOWBASE.COM ptype 1 (KRB5_NT_PRINCIPAL) vno 0 etype 0x12 (AES256-SHA1) keylength 32 (0xdd23498cd95fdb4b7ae7355b81c7999712bb4d590137af137922af97482ee45d)
keysize 76 HTTP/webserver-01.example.com@AD.IKNOWBASE.COM ptype 1 (KRB5_NT_PRINCIPAL) vno 0 etype 0x11 (AES128-SHA1) keylength 16 (0x4296070ee7889d4b26d15986f8190df4)
Move the keytab file you generated on the AD-server to the web server. Note that this is a sensitive file, since it can be used to log in on the AD-server: Use a secure transferring mechanism, and keep the file protected while on the web server.
Configure the Spnego module with the following settings: (More options are available)
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.spnego.enabled | true |
| com.iknowbase.spring.security.spnego.keytab | [PATH_TO]/iknowbase.webserver-01.example.com.krb5.keytab |
| com.iknowbase.spring.security.spnego.targetName | HTTP/webserver-01.example.com@AD.EXAMPLE.COM |
| com.iknowbase.spring.security.spnego.enabled | true |
| com.iknowbase.spring.security.spnego.debug | true (optional) |
Configure the LDAP UsernamePassword authentication provider: (More options are available)
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.ldap.enabled | true |
| com.iknowbase.spring.security.ldap.serverUrl | ldap://ad-server.example.com:389/DC=ad,DC=example,DC=com |
| com.iknowbase.spring.security.ldap.clientUserDn | CN=iknowbase.webserver-01.example.com,CN=Users,DC=ad,DC=example,DC=com |
| com.iknowbase.spring.security.ldap.clientUserPassword | SecretPassword!GlobalMilk |
| com.iknowbase.spring.security.ldap.userSearchBase.1 | CN=Users |
| com.iknowbase.spring.security.ikbauth.enabled | false (optional if you don’w want fallback to iKnowBase User Repository) |
Optionally, specify the LDAP sync profile. If this is specified, user synchronization will happend during login to add new users automatically. If it is ommited, a user who tries to log on must already exist in iKnowBase (typically through a scheduled LDAP Synch). The property “profile” is the externalKey of the “LDAP Sync” profile as specified in ikbStudio: (More options are available)
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.ldap.sync.enabled | true |
| com.iknowbase.spring.security.ldap.sync.profileExternalKey | ADSYNC_PROFILE_EXTERNALKEY |
Next, startup iKnowBase. The Spnego module will verify the settings when starting up. The results are logged to the configured log files.
Out of the box, all iknowbase objects are owned by a user called “orcladmin”. We recommend that you create a corresponding user in Active Directory, but you may also skip this step if you have enabled fallback authentication to iKnowBase User Repository:
For a user to be allowed access to iKnowBase, the user must exist in the iKnowBase user directory. This is done through a directory synchronization. Use the “LDAP Profile” to configure a profile, and “LDAP Sync” to configure synchronization frequency.
By default, logging in using Active Directory will expose the “sAMAccountName” attribute (the windows domain user account name) as the username in iKnowBase. This is the default behaviour, and most often the correct one.
In some scenarios, however, you may want to expose a different username to the iKnowBase application. For example, a new corporate directory may specify account names (login names) based on employee numbers (emp10523), while you want the iKnowBase application to use the historical usernames (which could be based on first initial and last name, e.g. “EPresley”). This is easily solvable, using the following steps:
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.ldap.ikbUsernameAttribute | ipPhone |
With this setup, a user logging in with the windows login “53310761” will be known as “EPresley” to iKnowBase.
The most frequently used setup is to have all users located in the same Active Directory subtree (in the examples at the beginning of this chapter, this is “CN=Users,DC=ad,DC=example,DC=com”). However, the iKnowBase security framework allows multiple user bases. The application uses the following logic when looking for these values:
com.iknowbase.spring.security.ldap.userSearchBase.1.
This is the simplest possible configuration (also the default), with a single userbase. For users in CN=Users,DC=ad,DC=example,DC=com (DC=ad,DC=example,DC=com is set as base in the LDAP server url)
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.ldap.userSearchBase.1 | CN=Users |
This a more complex configuration, with three userbases
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.ldap.userSearchBase.1 | CN=Employees |
| com.iknowbase.spring.security.ldap.userSearchBase.2 | CN=Premium Members |
| com.iknowbase.spring.security.ldap.userSearchBase.3 | CN=Basic Members |
You may use a combination of Active Directory and iKnowBase login. This is by default enabled. When enabled, the server and client will first attempt to do a single sign on using the Active Directory. If this fails, the client will ask for user information which will be used to first try LDAP authentication against the Active Directory and then authenticate against the internal iKnowBase user repository. This is useful for scenarios where certain administrative users (such as the “orcladmin” user) should not exist in Active Directory.
Building on the previous example, this mode is by default enabled, but you may disable the iKnowBase User Repository by setting
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.ikbauth.enabled | false |
You may add restrictions for which requests should trigger authentication negotiation. If negotiation is disabled due to a restriction, this module will fallback to a username and password based authentication.
To restrict the negotiation to a set of specific hosts:
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.spnego.serverNameExpr | webserver-01.example.com (server name from http request) |
To restrict the negotiation to a set of specific IP addresses (X-Forwarded-For IPs are supported):
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.spnego.remoteAddrExpr | ^10\..* |
iKnowBase web server only: To restrict the negotiation to the real immediate client IP (typically a reverse proxy):
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.spnego.realRemoteAddrExpr | ^192\.168\..* |
To restrict the negotiation to a specific request header (any request header):
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.spnego.requestHeaderName | User-Agent |
| com.iknowbase.spring.security.spnego.requestHeaderExpr |
.*Firefox/25.*
|
The default fallback mode if SPNEGO fails is using redirect to form based login where the user can provide username and password to be validated agains the enabled UsernamePassowrd providers (LDAP, iKnowBase).
If you want fallback to Basic authentication instead, set
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.spnego.sendAdditionalHttpBasicChallenge | true |
| com.iknowbase.spring.security.spnego.fallbackRedirectEnabled | false |
This will first send both a Negotiate and a Basic challenge. The client will normally try Negotiate if it supports SPNEGO. If SPNEGO fails, the next challenge will be Basic only.
The explicit authentication trigger
/ikb$auth/<authentication module>/authenticate supports the URL parameter
redirect. If the default module is Form based and you want to use the Basic trigger and be redirected to a specific URL afterwards, you would use
/ikb$auth/<authentication module>/authenticate?redirect=[Absolute_or_relative_url].
The Header authentication module can be used if you want to integrate with the Oracle SSO 10g platform. When using the Header authentication module it is extremely important that the trusted HTTP header is guaranteed by the reverse proxy in front of the iKnowBase web applications.
The header Osso-User-Dn must be guaranteed by the reverse proxyies in front of iKnowBase. The Oracle HTTP Server 10g does not have the capabilities to guarantee that the client cannot send this header, so you must have an additional reverse proxy in front of the Oracle HTTP Server 10g that removes the HTTP header Osso-User-Dn from all incoming requests.
The iKnowBase Web Application must be deployed to a server behind the Oracle HTTP Server with OSSO plugin and the following paths must be protected and require valid-user.
An example Oracle HTTP Server configuration:
NameVirtualHost *:7779
<VirtualHost *:7779>
Port 7778
ServerName example.iknowbase.com
RewriteEngine On
RewriteOptions inherit
OssoConfigFile /app/oracle/asPortal/Apache/Apache/conf/osso/osso_example.iknowbase.com.conf
OssoIpCheck off
<LocationMatch "^(/private|/ikbInstant/private|/ikb\$console|/ikb\$content|/ikb\$runner|/ikbWebServices)">
#HTTP Basic authentication
AuthType Basic
#We only require a valid user - no group/roles check
require valid-user
</LocationMatch>
ProxyPass / http://ikb-server.example.iknowbase.com:8080/
ProxyPassReverse / http://ikb-server.example.iknowbase.com:8080/
</VirtualHost>
Base configuration:
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.header.enabled | true |
| com.iknowbase.spring.security.header.headerNameUser | Osso-User-Dn |
| com.iknowbase.spring.security.header.headerNameUserExtractExpr |
^cn=([^,]+).+$
|
| com.iknowbase.spring.security.header.sendAdditionalHttpBasicChallenge | true |
| com.iknowbase.spring.security.header.unauthorizedStatusCode | 499 |
| com.iknowbase.spring.security.header.unauthorizedResponseHeaders | Osso-Paranoid:true |
If users can access the iKnowBase server directly over the network, you should add additional configuration to ensure the trusted requests must come from the Orache HTTP Server’s IP address:
| Property name | _Value |
|---|---|
| com.iknowbase.spring.security.header.realRemoteAddrExpr | [IP address to Oracle HTTP Server ] |
Authentication with ADFS is supported using SAML.
This example demonstrates SAML authentication on:
Prerequisites:
SAML connection leverage the social connection infrastructure, so we need to configure and enable that:
| Property name | _Value |
|---|---|
| com.iknowbase.spring.security.social.enabled | true |
| com.iknowbase.spring.security.social.encryptionPassword | <A password for sosial token encryption.> |
| com.iknowbase.spring.security.social.encryptionSalt | <Even number of 8 or more hex characters.> |
Create or reuse a Java keystore for SAML signing and encryption purposes. This example uses a private key with a self signed certificate with two year validity.
keytool -genkey -alias myprivatekeyalias1 -keyalg RSA -keystore <path_to_keystore>/keystore.jks -validity 720 -keysize 2048
<specify a keystore and a key passoword (may be the same)>
Configure iKnowBase with SAML and specify this keystore.
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.saml.enabled | true |
| com.iknowbase.spring.security.saml.keyManager.defaultKeyAlias | myprivatekeyalias1 (must be lower case) |
| com.iknowbase.spring.security.saml.keyManager.privateKey.1.alias | myprivatekeyalias1 (keyIndex = 1) (must be lower case) |
| com.iknowbase.spring.security.saml.keyManager.privateKey.1.password |
<password for myprivatekeyalias1> (keyIndex = 1)
|
| com.iknowbase.spring.security.saml.keyManager.storeFile |
<path to keystore/keystore.jks>
|
| com.iknowbase.spring.security.saml.keyManager.storePassword |
<password for keystore.jks>
|
Start iKnowBase and create service provider metadata using the SAML metadata generator at /ikb$auth/saml/generate (requires admin privileges). The default settings in the generator are normally sufficient, but please check if the identity provider administrator has any special requirements.
The generator displays an XML file containing the SAML service provider metadata. Store the file a file system reachable by the application server.
The generator also displays the configuration needed. Add to iKnowBase Installation properties (or set in any other of the supported property areas). The metadataProvider index must be chosen – select the first available index >=1 (if this is the first provider added, use index 1).
Download the ADFS metadata from https://YOUR_ADFS_SERVER/FederationMetadata/2007-06/FederationMetadata.xml and store the file a file system reachable by the application server.
Add the identity provider to the iKnowBase configuration with the next available metadata provider index (if the SP was .1, this should be .2).
| Property name | Value |
|---|---|
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpLoginFormShortName
|
<Name to display on form login button>
|
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpProviderEntityId
|
<Entity ID in ADFS XML metadata, i.e http://YOUR_ADFS_SERVER/adfs/services/trust
|
com.iknowbase.spring.security.saml.metadataProvider.
<index>.providerEntityType
|
IdP |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.resourcePath
|
<path to ADFS XML metadata>
|
The iKnowBase service provider metadata must be registered in the ADFS identity provider.
Select properties for the newly added relying party trust and set the secure hash algorithm in the advanced tab. Match the iKnowBaser service provider metadata (defaults to SHA-1).
Edit claim rules for the newly added relying party trust and add a new issuance transform rule.
iKnowBase supports using the iKnowBase Auth Token for linking iKnowBase and external user accounts. See description of the iKnowBase Auth Token “ACTIVATION”. The default iKnowBase setting will link using the provided Name ID, but you may also configure it to use a specific claim attribute instead.
iKnowBase also supports automatic account linking IF the identity provider can assert a claim containing the iKnowBase username. The default iKnowBase setting will link using the provided Name ID, but you may also configure it to use a specific claim attribute instead. Automatic linking is enabled using:
| Property name | Value |
|---|---|
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpAccountAutoConnectEnabled
|
true |
Setup is now complete and a login button for the identity provider has been added to the login form provided by iKnowBase on /ikb$auth/form/show.
Saml is by default not the default authentication provider, but you may choose to set it as the default by configuring “Saml” as the default module.
This is an example implementation of the switch user procedures.
create or replace
package custom_switch_user is
procedure access_check (p_switch_user ot_switch_user, p_return_code out number, p_return_message out varchar2);
procedure audit_user (p_switch_user ot_switch_user);
end;
/
create or replace
package body custom_switch_user is
procedure access_check (p_switch_user ot_switch_user, p_return_code out number, p_return_message out varchar2) is
begin
-- log to IKB_ERROR_TAB
ikb_common_procs.log_error('CUSTOM_SWITCH_USER.ACCESS_CHECK','authenticated_username: '||p_switch_user.authenticated_username||', '||
'switch_to_username: '||p_switch_user.switch_to_username);
-- implement access check logic here
p_return_code := 0; -- permit access
end;
procedure audit_user (p_switch_user ot_switch_user) is
begin
-- log to IKB_ERROR_TAB
ikb_common_procs.log_error('CUSTOM_SWITCH_USER.AUDIT_USER','authenticated_username: '||p_switch_user.authenticated_username||', '||
'switch_to_username: '||p_switch_user.switch_to_username||' switch_type = '||p_switch_user.switch_type);
-- do more logging / registrations here, if you need to
end;
end;
/
The steps needed to enable social authentication with user activation link and default form authentication are:
| Property name | _Value |
|---|---|
| com.iknowbase.spring.security.social.enabled | true |
| com.iknowbase.spring.security.social.encryptionPassword | <A password for sosial token encryption.> |
| com.iknowbase.spring.security.social.encryptionSalt | <Even number of 8 or more hex characters.> |
com.iknowbase.spring.security.social.
<provider>.enabled
|
true |
com.iknowbase.spring.security.social.
<provider>.clientId
|
<API key from the application registration> |
com.iknowbase.spring.security.social.
<provider>.clientSecret
|
<API secret from the application registration> |
| com.iknowbase.spring.security.ikbauthtoken.activation.enabled | true |
When inviting users to activate / connect using a social account, you’ll need to implement
A wildcard instance qualifier for a configuration option will match all applications. As an example, if you only want to match a specific application, set the instance qualifier to match the context path (“/” or “/MyCustomContextRoot”). See _Installation Guide > Configuration > The ikb_installation_properties table > Qualifier_
All these messages points to that you will need to update the java installation to handle higher security levels.
You will encounter this requirement if you use any of the following:
Download and install “Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files” from http://www.oracle.com/technetwork/java/javase/downloads/index.html.
For all these messages:
Both encryption password and salt must be configured in the social module.
The configured encryption salt set using configuration property “com.iknowbase.spring.security.social.encryptionSalt” must be set to a non empty even number of hex characters.
LDAP sync log can be viewed in /ikb$console/development/advanced/ldapsync. Select your sync profile and go to the “show log” tab.
When using the
idpIkbUsernameAttribute setting with ADFS, make sure that you use the claim type as
idpIkbUsernameAttribute and NOT the name.
Example:
SAML require the social connection infrastructure. Please review documentation for the ADFS sample and enable social login (no external social providers needed).
Java 8 has by default disabled weak crypto and will by default not support DES-CBC-MD5. A stronger encryption mechanism is strongly recommended. It is still possible to allow the weak crypto mechanisms by editing krb5.conf and setting allow_weak_crypto to true.
See The Kerberos 5 GSS-API Mechanism for more information.
WebLogic will by default intercept and validate HTTP Basic credentials even if the resource is not protected by WebLogic (iKnowBase is not). To allow HTTP basic credentials to pass through WebLogic to iKnowBase Spring Security, see WebLogic documentation on Understanding BASIC Authentication with Unsecured Resources .
Application security in iKnowBase relies on the Spring Security Framework and provides multiple modules for authentication and authorization.
See iKnowBase Installation Guide > Web Application Security for additional explanations.
See [Application context path]/ikb$console/config/configurations for default and active web application security configuration. All sections start with
com.iknowbase.spring.security.
Spring Security provides a debug mode documented as:
"Enables Spring Security debugging infrastructure. This will provide human-readable (multi-line) debugging information to monitor requests coming into the security filters. This may include sensitive information, such as request parameters or headers, and should only be used in a development environment."
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.debug | Enable or disable Spring Security debug mode |
For debugging, you may also want to enable trace logging adjust the logger levels to trace for
org.springframework.security and
com.iknowbase.spring.security.
Note that this particular debug flag is not visible under /ikb$console/config/configurations.
iKnowBase supports having multiple active authentication modules at the same time and these can be explicitly triggered, however, one must be set as the default.
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.init.defaultAuthenticationModule | Name of the authentication module to use as the default |
Module specific configuration is provided in the following sections.
No configuration options available.
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.container.enabled | Enable or disable module. Should not be necessary to change this setting. |
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.form.loginPageURL | Login URL (absolute or relative). |
| com.iknowbase.spring.security.form.loginErrorURL | Error URL (absolute or relative) if authentication does not succeed. |
| com.iknowbase.spring.security.form.rememberMeEnabled | Enable (true) or disable (false) RememberMe functionality. |
| com.iknowbase.spring.security.form.rememberMeTokenValiditySeconds | RememberMe token cookie validity in seconds. |
| com.iknowbase.spring.security.form.rememberMeTokenCleanupThresholdSeconds | RememberMe token cookie cleanup threshold in seconds. Must be higher than the highest token validity for this iKnowBase database repository. |
| com.iknowbase.spring.security.form.rememberMeCookieName | Set the cookie name used for RememberMe tokens. |
| com.iknowbase.spring.security.form.rememberMeCookiePath | Set the cookie path used for RememberMe tokens. Defaults to / (all apps on host). |
| com.iknowbase.spring.security.form.rememberMeCookieDomain | Set the cookie domain used for RememberMe tokens. Defaults is to send the cookie to the full host name that issued it. |
com.iknowbase.spring.security.form.exceptionMapping.
<index>
|
Authentication exception to url mapping.
Exception full class name:url to redirect to.
|
| com.iknowbase.spring.security.form.webdavFormLoginEnabled | Enable (true) or disable (false) form based login for WebDAV. Defaults to false. |
| com.iknowbase.spring.security.form.webdavFormLoginPageURL | Login URL (absolute or relative) for the form based login page. Defaults to standard form login page with RememberMe disabled. |
| com.iknowbase.spring.security.form.webdavFormLoginTriggerURL | Login URL (absolute or relative) with redirect to success URL for WebDAV. |
| com.iknowbase.spring.security.form.webdavFormLoginSuccessURL | Success URL (absolute or relative). MUST match the URL the user is redirected to if authentication succeeds. |
| com.iknowbase.spring.security.form.webdavFormLoginDialogSize | Dialog size for the form authentication dialog. Defaults to “800x600”, i.e. width=800px,height=600px. |
| com.iknowbase.spring.security.form.webdavFormLoginUserAgentExpr | Regular expression for matching browser’s User-Agent for WebDAV form based authentication. Defaults to all Microsoft Office clients. |
No configuration options available.
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.header.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.header.serverNameExpr | Regular expression restriction matching against the host name of the server to which the request was sent. |
| com.iknowbase.spring.security.header.remoteAddrExpr | Regular expression restriction matching against the end client’s IP address. |
| com.iknowbase.spring.security.header.realRemoteAddrExpr | Regular expression restriction matching against the immediate client’s IP address (typically a reverse proxy). ONLY available for iKnowBase web server. |
| com.iknowbase.spring.security.header.headerNameUser | Name of HTTP request header containing the authenticated username. |
| com.iknowbase.spring.security.header.headerNameUserExtractExpr | If necessary, specify a regular expression for extracting the username from the specified request header’s value. |
| com.iknowbase.spring.security.header.headerNameSecret | Name of HTTP request header containing the authentication shared secret. |
| com.iknowbase.spring.security.header.headerValueSecret | Value of the shared authentication secret (if any). |
| com.iknowbase.spring.security.header.authSchemeName | The scheme name in use when the server sends an authentication challenge. |
| com.iknowbase.spring.security.header.sendAdditionalHttpBasicChallenge | Also send a HTTP Basic authentication challenge. |
| com.iknowbase.spring.security.header.unauthorizedStatusCode | HTTP response status code for authentication challenge. |
| com.iknowbase.spring.security.header.unauthorizedResponseHeaders | Pipe delimited set of response headers. |
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.spnego.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.spnego.serverNameExpr | Regular expression restriction matching against the host name of the server to which the request was sent. |
| com.iknowbase.spring.security.spnego.remoteAddrExpr | Regular expression restriction matching against the end client’s IP address. |
| com.iknowbase.spring.security.spnego.realRemoteAddrExpr | Regular expression restriction matching against the immediate client’s IP address (typically a reverse proxy). ONLY available for iKnowBase web server. |
| com.iknowbase.spring.security.spnego.requestHeaderName | HTTP request header (if any) that must be present on the request for spnego to be enabled. |
| com.iknowbase.spring.security.spnego.requestHeaderExpr | Regular expression for validating the specified HTTP request header. |
| com.iknowbase.spring.security.spnego.keytab | Path to keytab file. |
| com.iknowbase.spring.security.spnego.targetName | targetName corresponding to the name registered in keytab (HTTP/[NAME]@[DOMAIN]). |
| com.iknowbase.spring.security.spnego.sendAdditionalHttpBasicChallenge | Also send a HTTP Basic authentication challenge. |
| com.iknowbase.spring.security.spnego.fallbackRedirectEnabled | Fallback to form based authentication instead of authentication challenge if spnego cannot be completed. |
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.ldap.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.ldap.serverUrl | URL to ldap server. May use LDAPS. TLS is not supported. |
| com.iknowbase.spring.security.ldap.clientUserDn | Full DN for client ldap user used for user lookup. |
| com.iknowbase.spring.security.ldap.clientUserPassword | Password for client ldap user. |
com.iknowbase.spring.security.ldap.userSearchBase.
<index>
|
Search base for users within the base dn given in server url. Index >= 1. Will search subtree from this base. |
| com.iknowbase.spring.security.ldap.usernameAttribute | Attribute matching the authentication username submitted by the web client. |
| com.iknowbase.spring.security.ldap.ikbUsernameAttribute | Attribute used as iKnowBase authenticated user. |
The LDAP provider may also be used in conjunction with the LDAP sync service. If the user was not found, the LDAP sync service will make an attempt at synchronizing the user into the iKnowBase User Repository.
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.ldap.sync.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.ldap.sync.profileExternalKey | External key to LDAP synchronization profile defined in iKnowBase. |
| com.iknowbase.spring.security.ldap.sync.executionUserName | Execution user. Should normally not be changed. |
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.ikbauth.enabled | Enable (true) or disable (false) module. |
See also: Spring Security SAML documentation .
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.saml.defaultFailureUrl | URL to redirect to in case of authentication failure. |
| com.iknowbase.spring.security.saml.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.saml.idpSelectionURL | URL presenting available SAML identity providers for login if not using the default or custom login form |
| com.iknowbase.spring.security.saml.keyManager.defaultKeyAlias | Default key alias to use for signing and encryption |
com.iknowbase.spring.security.saml.keyManager.privateKey.
<keyIndex>.alias
|
Alias for the private key in the key store. Configuration index >= 1. |
com.iknowbase.spring.security.saml.keyManager.privateKey.
<keyIndex>.password
|
Password for the private key in the key store. Configuration index >= 1. |
| com.iknowbase.spring.security.saml.keyManager.storeFile | Path to the Java keystore containg private key(s). |
| com.iknowbase.spring.security.saml.keyManager.storePassword | Password for accessing the Java keystore. |
| com.iknowbase.spring.security.saml.loginDefaultTargetUrl | Default URL to redirect to if no saved request was found after successful login. Defaults to / |
| com.iknowbase.spring.security.saml.logoutDefaultTargetUrl | Default URL to redirect to if no saved request was found after successful logout. Defaults to / |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.enabled
|
Enable (true) or disable (false) provider. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.requireArtifactResolveSigned
|
If true, received artifactResolve messages will require a signature, sent artifactResolve will be signed. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.requireLogoutRequestSigned
|
If true logoutRequests received will require a signature, sent logoutRequests will be signed. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.requireLogoutResponseSigned
|
Flag indicating whether entity in question requires logout response to be signed.. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.alias
|
Alias for choosing a specific service provider (if more than one). |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.encryptionKey
|
Alias to private key used for encryption |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.idpDiscoveryEnabled
|
Enable (true) or disable (false) identity provider discovery mode. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.idpDiscoveryResponseURL
|
Identity provider discovery response URL. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.idpDiscoveryURL
|
Identity provider discovery URL. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.local
|
If true, entity is treated as locally deployed and will be able to accept messages on endpoints determined by the selected alias. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.securityProfile
|
metaiop = “Uses cryptographic data from the metadata document of the entity in question. No checks for validity or revocation of certificates is done in this mode. All keys must be known in advance”. pkix = Signatures are deemed as trusted when credential can be verified using PKIX with trusted keys of the peer configured as trusted anchors. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.signMetadata
|
Flag indicating whether local metadata will be digitally signed. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.signingAlgorithm
|
Algorithm used for creation of digital signatures of this entity. Only used for metadata signatures. Only valid for local entities. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.signingKey
|
Signing key used for signing messages or verifying signatures of this entity. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.sslHostnameVerification
|
Hostname verifier to use for verification of SSL connections, e.g. for ArtifactResolution. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.sslSecurityProfile
|
Security profile used for SSL/TLS connections of the local entity. metaiop or pkix. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.tlsKey
|
Key used to authenticate instance against remote peers when specified on local entity. When specified on remote entity the key is added as a trust anchor during communication with the entity using SSL/TLS. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.extended.trustedKeys
|
Pipe delimited string of key alias for keys included as trusted anchors during PKIX evaluation. All keys in the keyStore are used as trust anchors with null value. Keys are only used with PKIX security profile. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpAccountAutoConnectEnabled
|
Enable (true) or disable false) automatic connect/link between iKnowBase and external user account. The iKnowBase username must be present in the SAML response (claim) using Name ID or a specific attribute. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpAccountSignupUrl
|
If no linked account could be found, redirect the user to this URL. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpIkbUsernameAttribute
|
iKnowBase username attribute in SAML response (claim). Defaults to Name ID claim. Custom attributes for ADFS uses the claim type defined in ADFS > Service > Claim Descriptions. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpLoginFormCssClass
|
iKnowBase default login form: Specify css class for the login button. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpLoginFormShortName
|
iKnowBase default login form: Specify name that will appear on the login button. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.idpProviderEntityId
|
EntityID, as specified in the provider’s metadata XML. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.metadataRequireSignature
|
When set to true metadata from this provider should only be accepted when correctly signed and verified. Metadata with an invalid signature or signed by a not-trusted credential will be ignored. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.metadataTrustCheck
|
If enabled, verifies metadata signature using pkix signature trust engine. |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.providerEntityType
|
Type of provider. SP = Service Provider. IdP = Identity Provider |
com.iknowbase.spring.security.saml.metadataProvider.
<index>.resourcePath
|
File system path to XML metadata for this provider. |
| com.iknowbase.spring.security.saml.metadataProvider.hostedSpName | Name of the default service provider for this application. Must match Entity ID of the service provider. |
| com.iknowbase.spring.security.saml.metadataProvider.spSelectionStrategy | Strategy for selecting Service Provider. SERVER_NAME or ALIAS_PATH. Defaults to SERVER_NAME (HTTP Request ServerName), which must match Entity ID of the service provider. |
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.social.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.social.socialSignupURL | Signup URL (absolute or relative) to redirect the user to if the social authentication attempt did not match an iKnowBase user account. |
| com.iknowbase.spring.security.social.socialProvidersEnabled | Comma separated list of providers. Used when rendering login and activation page. Defaults to all enabled providers. |
| com.iknowbase.spring.security.social.encryptionPassword | Password used when encrypting social authentication tokens before they are persisted to database. Required if you enable social authentication. |
| com.iknowbase.spring.security.social.encryptionSalt | Salt, which must be an even number of 8 or more hex characters. Used when encrypting social authentication tokens before they are persisted to database. Required if you enable social authentication. |
Google specific configuration:
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.social.google.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.social.google.clientId | Client ID registered with the social provider. |
| com.iknowbase.spring.security.social.google.clientSecret | Client Secret registered with the social provider |
| com.iknowbase.spring.security.social.google.scope | OAuth scope for requesting permissions with the social provider. Default will enable authentication. |
Twitter specific configuration:
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.social.twitter.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.social.twitter.clientId | API Key registered with the social provider. |
| com.iknowbase.spring.security.social.twitter.clientSecret | API Secret registered with the social provider |
| com.iknowbase.spring.security.social.twitter.scope | OAuth scope for requesting permissions with the social provider. Default will enable authentication. |
Facebook specific configuration:
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.social.facebook.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.social.facebook.clientId | App ID registered with the social provider. |
| com.iknowbase.spring.security.social.facebook.clientSecret | App Secret registered with the social provider |
| com.iknowbase.spring.security.social.facebook.scope | OAuth scope for requesting permissions with the social provider. Default will enable authentication. |
LinkedIn specific configuration:
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.social.linkedin.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.social.linkedin.clientId | API Key registered with the social provider. |
| com.iknowbase.spring.security.social.linkedin.clientSecret | Secret Key registered with the social provider |
| com.iknowbase.spring.security.social.linkedin.scope | OAuth scope for requesting permissions with the social provider. Default will enable authentication. |
Microsoft Live / Microsoft account specific configuration:
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.social.live.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.social.live.clientId | API Key registered with the social provider. |
| com.iknowbase.spring.security.social.live.clientSecret | Secret Key registered with the social provider |
| com.iknowbase.spring.security.social.live.scope | OAuth scope for requesting permissions with the social provider. Default will enable authentication. |
Note: The iKnowBase Secure Token Engine configuration is described in SecureTokenEngine
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.securetoken.maxAgeSeconds | Max age allowed when validating the iKnowBase secure token. |
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.authentication.ikbpublic.anonymousKey | Shared key used by the anonymous authentication provider. Should normally not be set. |
All authentication attempts must ultimately load a user from the iKnowBase User Repository before the authentication is fully accepted.
| Property name | Description |
|---|---|
| com.iknowbase.spring.security.userdetails.executionUserName | Execution user. Should normally not be changed. |
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.switchuser.enabled | Enable (true) or disable (false) module. |
| com.iknowbase.spring.security.switchuser.accessCheckProcedureName | Name of check access database procedure. |
| com.iknowbase.spring.security.switchuser.auditProcedureName | Name of audit database procedure (optional) |
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.activation.showActivationOptionsURL | Activation options URL (absolute or relative) to redirect the user to if a valid activation token is presented. |
| com.iknowbase.spring.security.activation.activationFailedURL | Failure URL (absolute or relative) to redirect the user to if the user presented an invalid activation token. |
| com.iknowbase.spring.security.activation.ikbProviderSetPasswordEnabled | Enable users with activation token to set the user’s password in the iKnowBase User Repository. |
| com.iknowbase.spring.security.activation.ikbProviderSetPasswordAlgorithm | Override default password encryption algorithm when setting password. |
| Property name | Value |
|---|---|
| com.iknowbase.spring.security.ikbauthtoken.activation.enabled | Enable (true) or disable (false) processing of token type ACTIVATION. |
| com.iknowbase.spring.security.ikbauthtoken.login.enabled | Enable (true) or disable (false) processing of token type LOGIN. |
| Previous | Top | Next |
| Instant module | Apache Solr Search Server |